Zero-day #5 in 2017 targets Microsoft Word users

McAfee disclosed on Friday information about zero-day exploit (SB2017040901) targeting Microsoft Office users. The malicious file in question is an RTF document with .doc extension and embedded OLE2link object. FireEye confirmed the existence of the vulnerability by posting an acknowledgment in their blog post on April8, 2017.
The attackers use a specially crafted RTF document, which once opened, makes the winword.exe to issue a HTTP request to a remote server to retrieve a malicious .hta file. Currently there are two discovered malicious documents serving this exploit. In both cases, the exploit code terminates the winword.exe process to hide a user prompt generated by the OLE2link.
According to McAfee, vulnerability can be exploited against all versions of Microsoft Word, including Microsoft Office 2016 on Windows 10.
This is the fifth zero-day vulnerability this year, but the first one disclosed by a third party instead of the software vendor and the second one still unpatched.
Microsoft Word is one of the most popular targets for file-based exploits among other Microsoft Office components. The diagram below shows distribution of zero-day vulnerabilities in Microsoft Office components for 2006-2016:
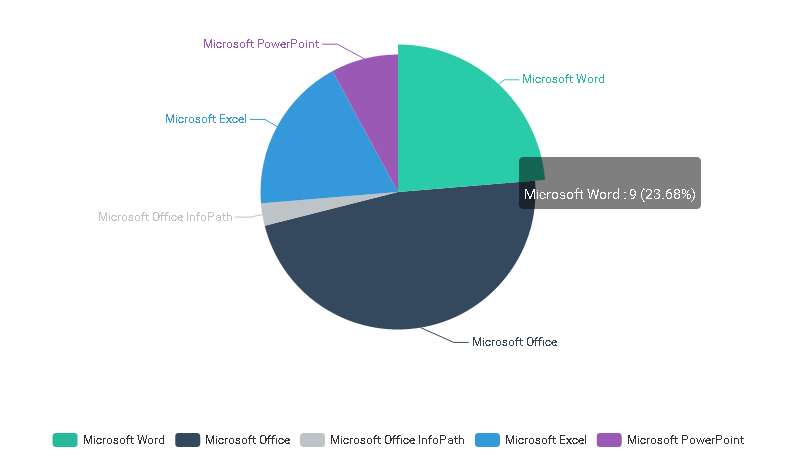
Zero-day vulnerabilities in MS Office (2006-2016)
Hopefully Microsoft will patch this vulnerability during the next Patch Tuesday on April, 11.
We advise all users to install the patch as soon as it is available.
UPDATE
Since there are questions about zero-day vulnerabilities in 2017, I have decided to update this post with this information. So here they are:
CVE-2017-0005 (SB2017031505) - The vulnerability was used by Zirconium cyber-espionage group against older versions of Windows. Reported by Microsoft as a zero-day.
CVE-2017-0022 (SB2017031404) - This vulnerability was used in the AdGholas malvertising campaign and later integrated into the Neutrino exploit kit. The vulnerability was reported to Microsoft in September 2016. The first malware sample, discovered in the wild, is connected with AdGholas campaign in July 2016. The exploit came back again in September 2016 with the Neutrino exploit kit.
CVE-2017-0149 (SB2017031409) – reported by Microsoft as a zero-day. Information about targets was not disclosed yet.
CVE-2017-3881 (SB2017031702) – The vulnerability was disclosed by WikiLeaks in documents dubbed CIA Vault 7. It is believed that this vulnerability was used by CIA agents to penetrate government and corporate networks. Reported by Cisco.
SB2017040901 – The latest zero-day. The earliest attack dates to late January, according to McAfee.
Latest Posts

Iranian hackers exploit RMM tools to deliver malware
One of the aspects of MuddyWater's strategy involves exploiting Atera's free trial offers.
Ongoing malware campaign targets multiple industries, distributes infostealers
The campaign leverages a CDN cache domain as a download server, hosting malicious HTA files and payloads.
US charges four Iranian hackers for cyber intrusions
The group targeted both both government and private entities.
| 24 Apr, 2024