Security is not a process. It's a state until you get pwned (c)
We are extremely glad to announce the official opening of Free Zero-Day Vulnerability Tracking Project, aimed to disclose and make publicly available information on all zero-day vulnerabilities ever used in the wild. For now, the database contains description of 353 zero-day vulnerabilities exploited since 2006.
Our research covers vulnerabilities of the most dangerous kind - the ones that are unknown to anybody except the malicious actor. Once they are used in a properly engineered attack there is no way to stop the hack. In the past decade we have witnessed sophisticated crimes, perfectly planned, organized and executed by the real Kung Fu masters of keyboard, mouse and espionage.
During our research we have gathered and analyzed publicly available information about almost 100 APT campaigns and reports on more than 500 vulnerabilities, suspected to be exploited in the wild both in targeted and mass attacks. As data sources we have used vulnerability databases, reports from companies and researchers in the field, news articles, official statements, etc. For comparison purposes we have chosen yearly reports from major IT security market players, who publish zero-day vulnerability statistics, such as Symantec, Trustwave, Flexera/Secunia, and FireEye.
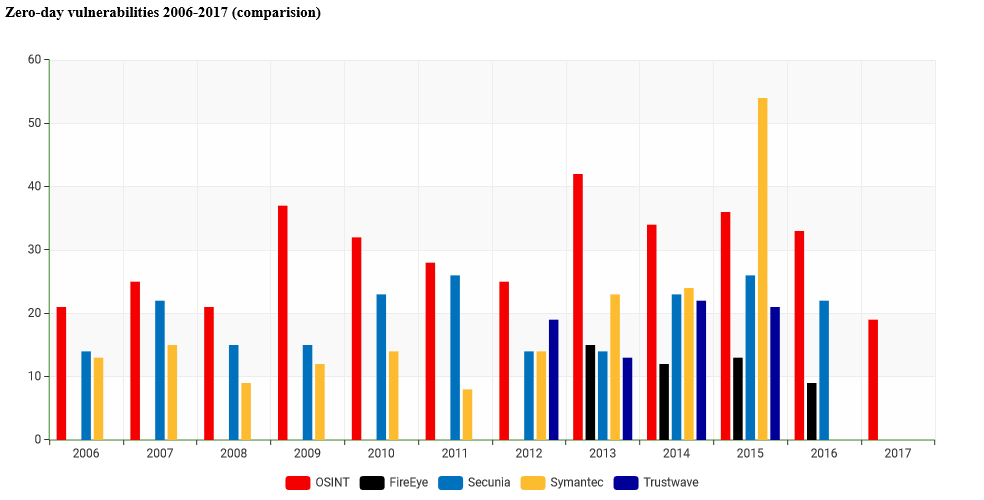
Below is comparison statistics for reported zero-days by different security companies and our research under OSINT abbreviation in red color.
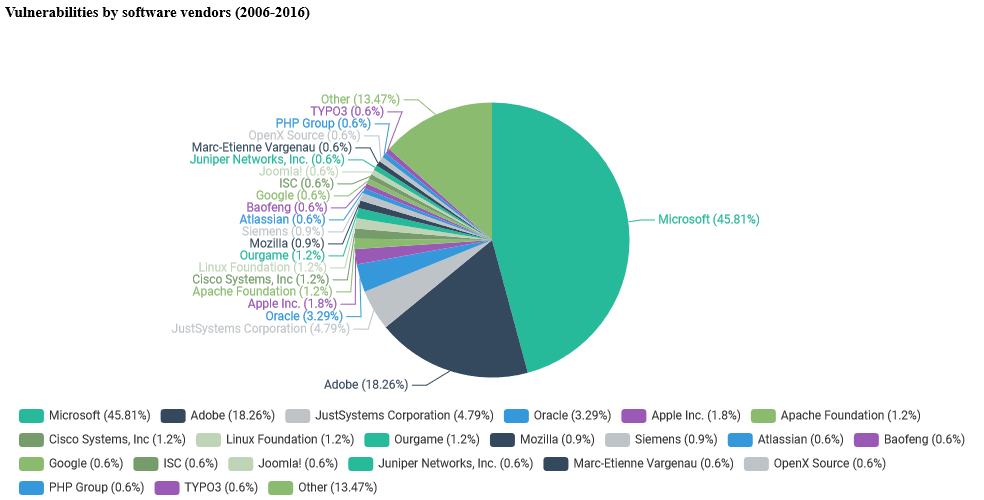
The largest number of zero-day vulnerabilities was reported in Microsoft products - 46% of all zero-days. The second closest vendor is Adobe with just 18% of the "market".
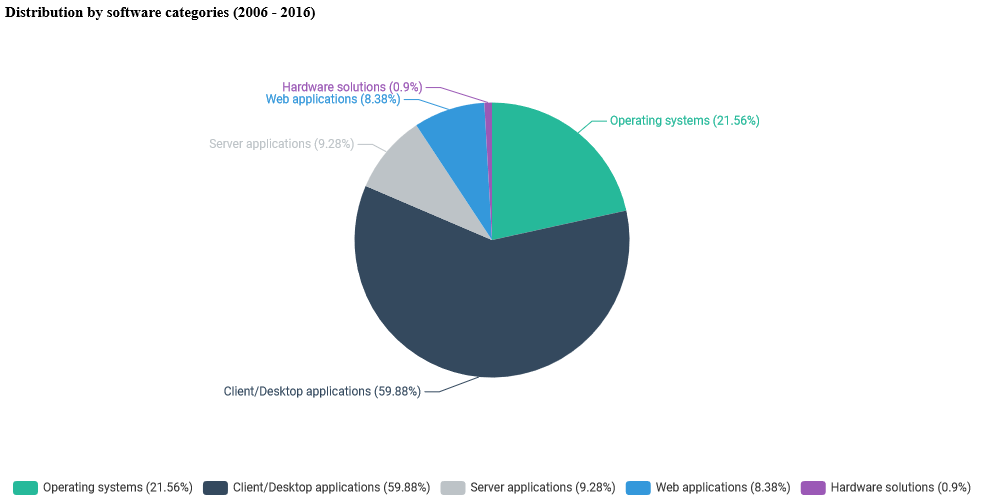
At the same time, the malware developers chose office applications as the most popular attack vector (73 zero-days) and operating system components (72 zero-days). The third place is taken by the number of exploits against browser-based plugins (e.g. ActiveX components, Adobe Flash player, Silverlight, etc.) - 57 in total. Along with web browsers (41 zero-days) they cover 73% of all vulnerabilities used in the wild.
All APT campaigns, analyzed during this research, were perfectly organized and significantly financed. And we do not believe these were crowdfunding projects from Kikstarter =) The only logical conclusion is that all of the espionage campaigns were planned, sponsored and executed by intelligence services of different countries. The latest leaks presented by the WikiLeaks project made us even more sure of that.
The full research along with free access to vulnerability database: https://www.zero-day.cz/
Sincerely yours,
Valerii Marchuk
Microsoft MVP, founder of Cybersecurity Help s.r.o.