Interesting vulnerabilities in Microsoft products happen not that often. This time however we have patches for TWO zero-days in Windows and RCE in Microsoft Exchange. Something not very usual.
Zero-days
The first zero day was reported in April by 360 Core Security as vulnerability in Internet Explorer and was dubbed “double play” due to specific exploitation vector. According to new information, the bug resides within Microsoft VBScript engine and affects all supported Microsoft Windows operating systems.
The second zero-day vulnerability resides within win32k.sys driver and affects Windows 7 and Windows 2008/2008 R2 systems. Currently there isn’t much information about it apart that is seems ESET was the one who reported it.
Last year Microsoft patched 19 zero-days in their products. This year there are just 3 for Microsoft out of 10 in total.
RCE in Microsoft Exchange
Along with 3 XSS in OWA frontend Microsoft also fixed two memory corruption vulnerabilities in Microsoft Exchange engine: out-of-bounds read and buffer overflow. While the first vulnerability grants access to system memory, the second one may allow remote code execution and affects all supported versions of Microsoft Exchange. Both vulnerabilities can be exploited just by sending a specially crafted email message.
Attention: patch your Exchange server ASAP.
Office vulnerabilities
This month Microsoft fixed 10 vulnerabilities in Office applications. Most of them allow remote code execution.
Windows kernel
Along with other bugs vendor released coordinated patch for vulnerability CVE-2018-8897. This vulnerability exists due to faulty implementation of Intel 64 and IA-32 Architectures Software Developer's Manual (SDM) and affects multiple operating systems.
Some numbers
Vulnerabilities distribution by types
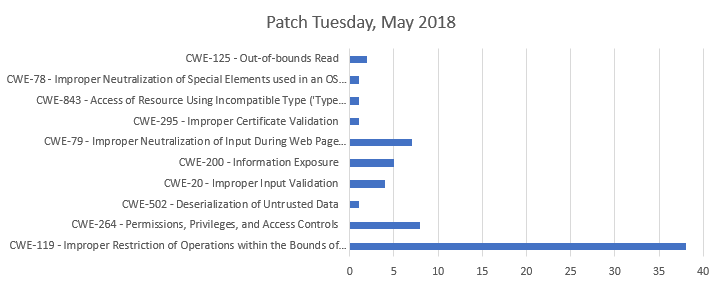
Diag. 1
As you can see, most of vulnerabilities are buffer-related errors (CWE-119, CWE-125).
Exploitation vector
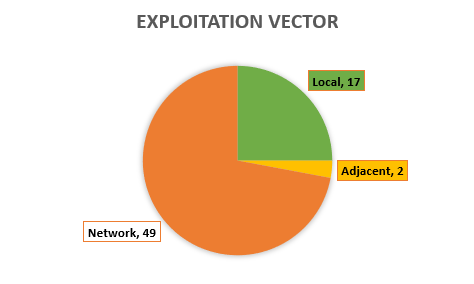
Diag. 2
72% of all vulnerabilities are remotely exploitable.
Vulnerabilities by severity
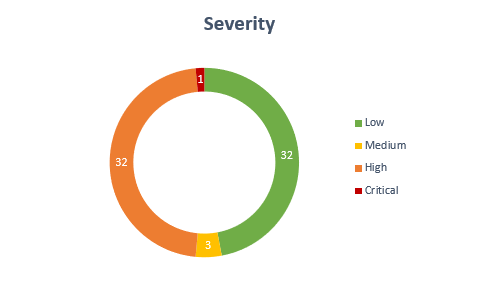
Diag. 3
49% of all vulnerabilities have high or critical severity level, which means that they allow remote code execution.
Here is the list of all patches released during this patch Tuesday:
| Software | Severity | CVE/CVSS | Known exploits |
| SB2018042106: Remote code execution in Microsoft VBScript engine (1) | |||
|
Windows Windows Server |
Critical |
CVE-2018-8174 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:H/RL:O/RC:C |
This vulnerability is being exploited in the wild. |
| SB2018050838: Privilege escalation in Microsoft Windows (1) | |||
|
Windows Windows Server |
Low |
CVE-2018-8897 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2018050837: Security restrictions bypass in Microsoft Windows (5) | |||
|
Windows Windows Server |
Low |
CVE-2018-0854 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:L/E:U/RL:O/RC:C CVE-2018-0958 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:L/E:U/RL:O/RC:C CVE-2018-8129 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:L/E:U/RL:O/RC:C CVE-2018-8132 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:L/I:L/A:L/E:U/RL:O/RC:C CVE-2018-8142 CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:L/E:U/RL:O/RC:C |
Not available |
| SB2018050836: Privilege escalation in Microsoft Windows Kernel API (1) | |||
|
Windows Windows Server |
Low |
CVE-2018-8134 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2018050835: Privilege escalation in Microsoft Windows Common Log File System driver (1) | |||
|
Windows Windows Server |
Low |
CVE-2018-8167 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2018050834: Privilege escalation in Microsoft Windows Image (1) | |||
|
Windows Windows Server |
Low |
CVE-2018-8170 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2018050833: Privilege escalation in Microsoft Windows (1) | |||
|
Windows Windows Server |
Low |
CVE-2018-8136 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2018050832: Privilege escalation in Microsoft Windows DirectX Graphics Kernel (DXGKRNL) driver (1) | |||
|
Windows Windows Server |
Low |
CVE-2018-8165 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2018050831: Remote code execution in Microsoft InfoPath (1) | |||
| Microsoft Office InfoPath | High |
CVE-2018-8173 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2018050830: Privilege escalation in Microsoft Windows Win32k (3) | |||
|
Windows Windows Server |
Low |
CVE-2018-8166 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8164 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8124 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2018050829: Remote code execution in Microsoft COM for Windows (1) | |||
|
Windows Windows Server |
High |
CVE-2018-0824 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2018050828: Multiple vulnerabilities in Microsoft Hyper-V (2) | |||
|
Windows Windows Server |
Medium |
CVE-2018-0961 CVSS:3.0/AV:A/AC:H/PR:H/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-0959 CVSS:3.0/AV:A/AC:H/PR:H/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2018050827: Information disclosure in Microsoft Windows Kernel (2) | |||
|
Windows Windows Server |
Low |
CVE-2018-8127 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:L/I:N/A:N/E:U/RL:O/RC:C CVE-2018-8141 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:L/I:N/A:N/E:P/RL:O/RC:C |
Public exploit code for vulnerability #2 is available. |
| SB2018050826: Multiple vulnerabilities in Microsoft Internet Explorer (9) | |||
| Microsoft Internet Explorer | High |
CVE-2018-8114 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-0955 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8122 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8126 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:L/A:L/E:U/RL:O/RC:C CVE-2018-8178 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-1022 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-1025 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:N/A:N/E:U/RL:O/RC:C CVE-2018-0954 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8145 CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N/E:U/RL:O/RC:C |
Not available |
| SB2018050825: Cross-site scripting in Microsoft Project Server (1) | |||
| Microsoft Project Server | Low |
CVE-2018-8156 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N/E:U/RL:O/RC:C |
Not available |
| SB2018050824: Multiple XSS vulnerabilities in Microsoft SharePoint Server (4) | |||
|
Microsoft SharePoint Server Microsoft SharePoint Foundation |
Low |
CVE-2018-8155 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N/E:U/RL:O/RC:C CVE-2018-8156 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N/E:U/RL:O/RC:C CVE-2018-8168 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N/E:U/RL:O/RC:C CVE-2018-8149 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N/E:U/RL:O/RC:C |
Not available |
| SB2018050823: Spoofing attack in Azure IoT SDK (1) | |||
|
C# SDK for Azure IoT C SDK for Azure IoT Java SDK for Azure IoT |
Low |
CVE-2018-8119 CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:C/C:L/I:L/A:N/E:U/RL:O/RC:C |
Not available |
| SB2018050822: Adobe Flash Security Update for Windows (1) | |||
| Adobe Flash Player | High |
CVE-2018-4944 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2018050821: Remote command execution in Microsoft Outlook 2016 (1) | |||
| Microsoft Office | High |
CVE-2018-8150 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2018050820: User credentials disclosure in Microsoft Outlook 2010 (1) | |||
|
Microsoft Office Microsoft Office Compatibility Pack Word Automation Services on Microsoft SharePoint Server Microsoft Office Web Apps Server |
High |
CVE-2018-8160 CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:N/A:N/E:U/RL:O/RC:C |
Not available |
| SB2018050819: Multiple vulnerabilities in Microsoft ChakraCore (13) | |||
| ChakraCore | High |
CVE-2018-8177 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8178 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-1022 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-0953 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-0943 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-0945 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-0946 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8130 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8133 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8137 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8139 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8128 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8145 CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N/E:U/RL:O/RC:C |
Not available |
| SB2018050818: Multiple vulnerabilities in Microsoft Edge (19) | |||
| Microsoft Edge | High |
CVE-2018-8179 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8123 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8112 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N/E:U/RL:O/RC:C CVE-2018-1021 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:N/A:N/E:U/RL:O/RC:C CVE-2018-8178 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-1022 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-0954 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-0953 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-0951 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-0946 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-0945 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-0943 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8139 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8137 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8133 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8130 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8128 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8145 CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N/E:U/RL:O/RC:C CVE-2018-1025 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:N/A:N/E:U/RL:O/RC:C |
Not available |
| SB2018050817: Multiple vulnerabilities in Microsoft Excel (4) | |||
|
Microsoft Excel Microsoft Office Microsoft Office for Mac Microsoft Office Compatibility Pack |
High |
CVE-2018-8162 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8163 CVSS:3.0/AV:N/AC:H/PR:N/UI:R/S:U/C:H/I:N/A:N/E:U/RL:O/RC:C CVE-2018-8147 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8148 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2018050816: Remote code execution in Microsoft Office (3) | |||
|
Microsoft Office Microsoft Word Microsoft SharePoint Server Word Automation Services on Microsoft SharePoint Server Microsoft Office Web Apps Microsoft Office Web Apps Server |
High |
CVE-2018-8161 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8157 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8158 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2018050815: Denial of service in Microsoft .NET Framework and ASP .NET Core (1) | |||
|
Microsoft .NET Framework ASP.NET Core MVC |
Medium |
CVE-2018-0765 CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:N/I:N/A:H/E:U/RL:O/RC:C |
Not available |
| SB2018050814: Security Feature Bypass in Microsoft .NET Framework (1) | |||
| Microsoft .NET Framework | Low |
CVE-2018-1039 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2018050813: Privilege escalation in Microsoft Windows win32k.sys driver (1) | |||
|
Windows Server Windows |
High |
CVE-2018-8120 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C |
This vulnerability is being exploited in the wild. |
| SB2018050812: Multiple vulnerabilities in Microsoft Exchange Server (5) | |||
| Microsoft Exchange Server | High |
CVE-2018-8154 CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2018-8151 CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:L/I:N/A:N/E:U/RL:O/RC:C CVE-2018-8159 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N/E:U/RL:O/RC:C CVE-2018-8152 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N/E:U/RL:O/RC:C CVE-2018-8153 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N/E:U/RL:O/RC:C |
Not available |