A recently found critical bug (CVE-2019-3396) in Atlassian Confluence Server is being actively exploited to compromise Linux and Windows servers with the purpose of infecting them with the different forms of malware namely AESDDoS botnet trojan and GandCrab ransomware, according to the reports from cybersecurity firms Trend Micro and Alert Logic.
CVE-2019-3396 is server-side template injection vulnerability, which is present in the Widget Connector macro in Atlassian Confluence Server, a collaboration software program used by DevOps professionals. This flaw allows attackers to remotely achieve path traversal and remote code execution on a Confluence Server or Data Center instance via server-side template injection. The bug affects Confluence Versions 6.6.0 – 6.6.11; 6.7.0 – 6.12.2; 6.13.0 – 6.13.2; 6.14.0 – 6.14.1 and was addressed in versions 6.6.12., 6.12.3., 6.13.3, and 6.14.2.
Multiple CVE-2019-3396 exploits are already available publicly and cybercriminals are actively using them to scan the internet for vulnerable servers and to install malware on unpatched machines.
In the attacks detected by Trend Micro threat actors attempt to install the Dofloo (aka AES.DDoS, Mr. Black) Trojan capable of performing distributed denial of service (DDoS) attacks, including SYN, LSYN, UDP, UDPS, and TCP flood, remote code execution, and crypto-currency mining. The attack involves the remote execution of a shell command to download and execute a malicious shell script (Trojan.SH.LODEX.J), which in turn would download another shell script (Trojan.SH.DOGOLOAD.J) that finally installed the AESDDoS botnet malware on the compromised system. This variant can also steal information on affected systems, such as model ID and CPU description, speed, family, model, and type. The collected data, as well as the command and control (C&C) data, is encrypted using the AES algorithm. Additionally, AESDDoS variant can modify files as an autostart technique by appending the {malware path}/{malware file name} reboot command.
In the campaigns observed by Alert Logic the attackers weaponized CVE-2019-3396 to infect the compromised machines with the GandCrab ransomware. Once gaining an access to vulnerable server, the attackers would download the Empire PowerShell post-exploitation toolkit and then use it to download a packed version of GandCrab with the help of CertUtil LOLBin (Living Off The Land Binary) - standard binaries which attackers often use to avoid detection.
Both Trend Micro and Alert Logic published full lists of indicators of compromise (IOCs) for the campaigns leveraging CVE-2019-3396:
Trend Micro:
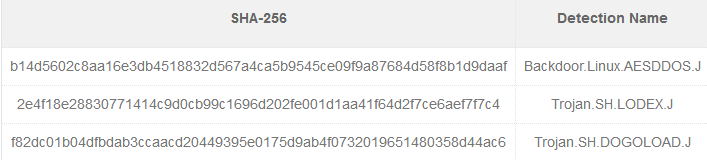
Alert Logic:
Command and Control servers
- 185[.]234[.]218[.]248
- 188[.]166[.]74[.]218
Pastebin PowerShell script
- hxxps://pastebin[.]com/raw/VKX98sKj
Hashes
- 1064e288b3bdc80e8017e6538ffb36a9384afabe3aef8fc48b1bf7b8136754b5 - gandcrab pastebin
- 18e67a910c6db2e05481c43c751ab07fab5d8fc36b3c747677d8619202a40ee1 - len.exe