Operation Sea Turtle compromises Greece domain admin, keeps looking for new victims
State-sponsored hackers compromised ICS-Forth (Institute of Computer Science of the Foundation for Research and Technology), the organisation that manages the top-level domains for Greece — .gr and .el — in April this year. The perpetrators behind the hack is the same group that previously compromised at least 40 different organizations across 13 different countries during the campaign dubbed Sea Turtle by security researchers.
In April 2019 Cisco Talos team has published an extensive report describing the campaign, but despite the exposure of their activities it appears that the hackers did not cease the operation. New evidence suggests that the threat actor has switched to a new infrastructure and is using another DNS hijacking technique.
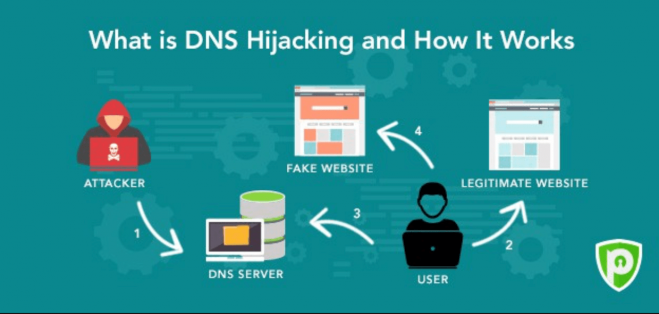
Sea Turtle group uses an interesting approach to hacking targets. Instead of targeting victims directly, they compromise accounts at domain registrars and managed DNS providers and change a company's DNS settings redirecting traffic meant for an organization’s legitimate apps or webmail services to servers under their control where they can carry man-in-the-middle attacks and capture login credentials. Usually attacks last only a few hours or days and and are hard to detect due to the fact that most companies don’t monitor for modifications made to DNS settings.
According to a new Cisco Talos’ report, the Sea Turtle group used the similar approach in attack against ICS-Forth network. The researchers did not reveal much details of the attack aside from that that the hackers maintained access to the network for another five days after ICS-Forth publicly disclosed the incident on April 19. At the moment it’s unclear what the attackers did on the network once they gained an access to ICS-Forth’s systems and what were the domain names for which hackers changed DNS settings.
“Cisco telemetry confirmed that the actors behind Sea Turtle maintained access to the ICS-Forth network from an operational command and control (C2) node. Our telemetry indicates that the actors maintained access in the ICS-Forth network through at least April 24, five days after the statement was publicly released. Upon analysis of this operational C2 node, we determined that it was also used to access an organization in Syria that was previously redirected using the actor-controlled name server ns1[.]intersecdns[.]com. This indicates that the same threat actors were behind both operations,” said the researchers.
As for the new DNS hijacking technique that the group was leveraging in the recent attacks, Cisco Talos said that it is similar to the previously used methods in that the threat actors compromise the name server records and respond to DNS requests with falsified A records. The experts also pointed out that this technique is rarely used and has only been observed in a few highly targeted operations. Additionally, Talos said they identified new victims located in countries such as Sudan, Switzerland, and the US. The list of targets includes government organizations, energy companies, think tanks, international non-governmental organizations, and at least one airport.
Latest Posts

China-linked LightSpy iOS implant re-emerges, targets South Asia
LightSpy contains modules designed to exfiltrate device information and saved files.
Cryptojacker indicted for defrauding cloud service providers of $3.5M
Parks allegedly manipulated the cloud providers into granting him elevated privileges and benefits.
Firebird RAT developers and sellers arrested in the US and Australia
The malware allows to remotely access victims' computers and perform illicit activities.