Vulnerability Intelligence Services
Cyber threats evolve daily, and outdated security measures leave businesses exposed to attacks. Our Vulnerability Intelligence service delivers real-time, actionable insights to help you stay ahead of potential risks before they become costly breaches.
Highlights from 2025
Real-time vulnerability intelligence at scale
Threat Monitor
- Automated analysis
- Real-time threat detection
- 24/7 monitoring of media and social networks
How Vulnerability Intelligence Works
From continuous monitoring to actionable insights
Continuous Monitoring
We track vulnerabilities across software, firmware, operating systems, OS packages, network devices in real time covering more than 60K software vendors and over 700K applications.
Comprehensive Vulnerability Database
Our platform aggregates data from multiple sources, such as vendor advisories, software changelogs, mailing lists, public vulnerability databases, forums, blogs, social and regular media, etc.
Risk-Based Prioritization
Not all vulnerabilities pose the same risk. Our analysts prioritize threats based on their exploitability, severity, and relevance.
Custom Alerts & Reports
Receive instant emails tailored to your specific software stack, risk tolerance, or compliance needs.
API Access for Seamless Integration
Connect our intelligence directly to your security tools and workflows for automated risk management.
Comprehensive Data Sources
We aggregate vulnerability data from multiple trusted sources
Vulnerability Databases
Vendor Advisories
Software Changelogs
Mailing Lists
Security Forums
Blogs
Social Media
Media Outlets
Why Choose Our Vulnerability Intelligence?
Trusted by security teams worldwide
Real-Time Updates
Never miss a critical vulnerability with up-to-the-minute data.
Personalized Intelligence
Filter alerts based on your technology stack and risk profile.
Actionable Insights
Go beyond raw data with expert analysis and remediation guidance.
Seamless Integration
API access ensures compatibility with SIEMs, SOCs, and other security tools.
Proven Expertise
Trusted by security teams worldwide for reliable and actionable intelligence.
Comprehensive Vulnerability Database
Our intelligence is powered by an extensive vulnerability database covering 60K+ software vendors and 700K+ applications. Explore our database to see the depth of our coverage.
Explore Vulnerability Database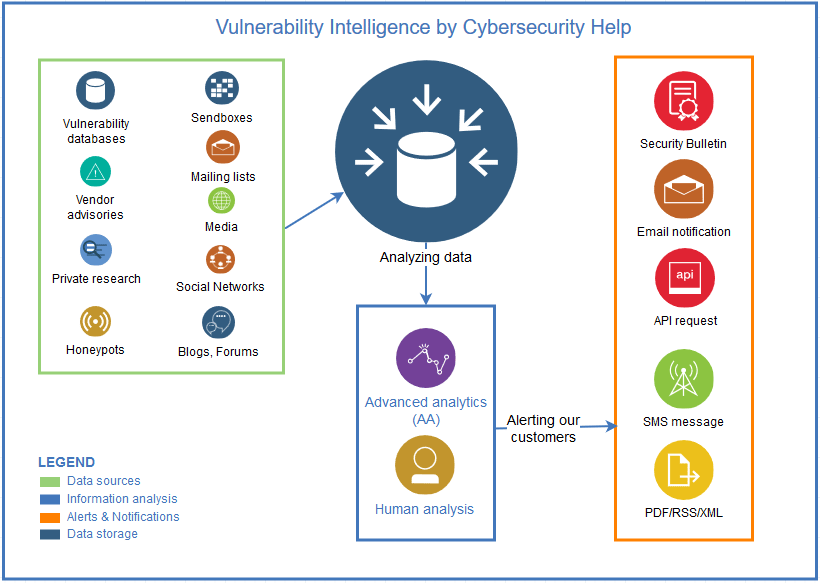
Try It for Free – No Commitment
Get a first-hand experience of how vulnerability intelligence can transform your security strategy. Sign up today for a free trial and start receiving customized alerts for the software you use.
Don't wait for an attack to expose your weaknesses. Take a proactive approach to cybersecurity with Vulnerability Intelligence.