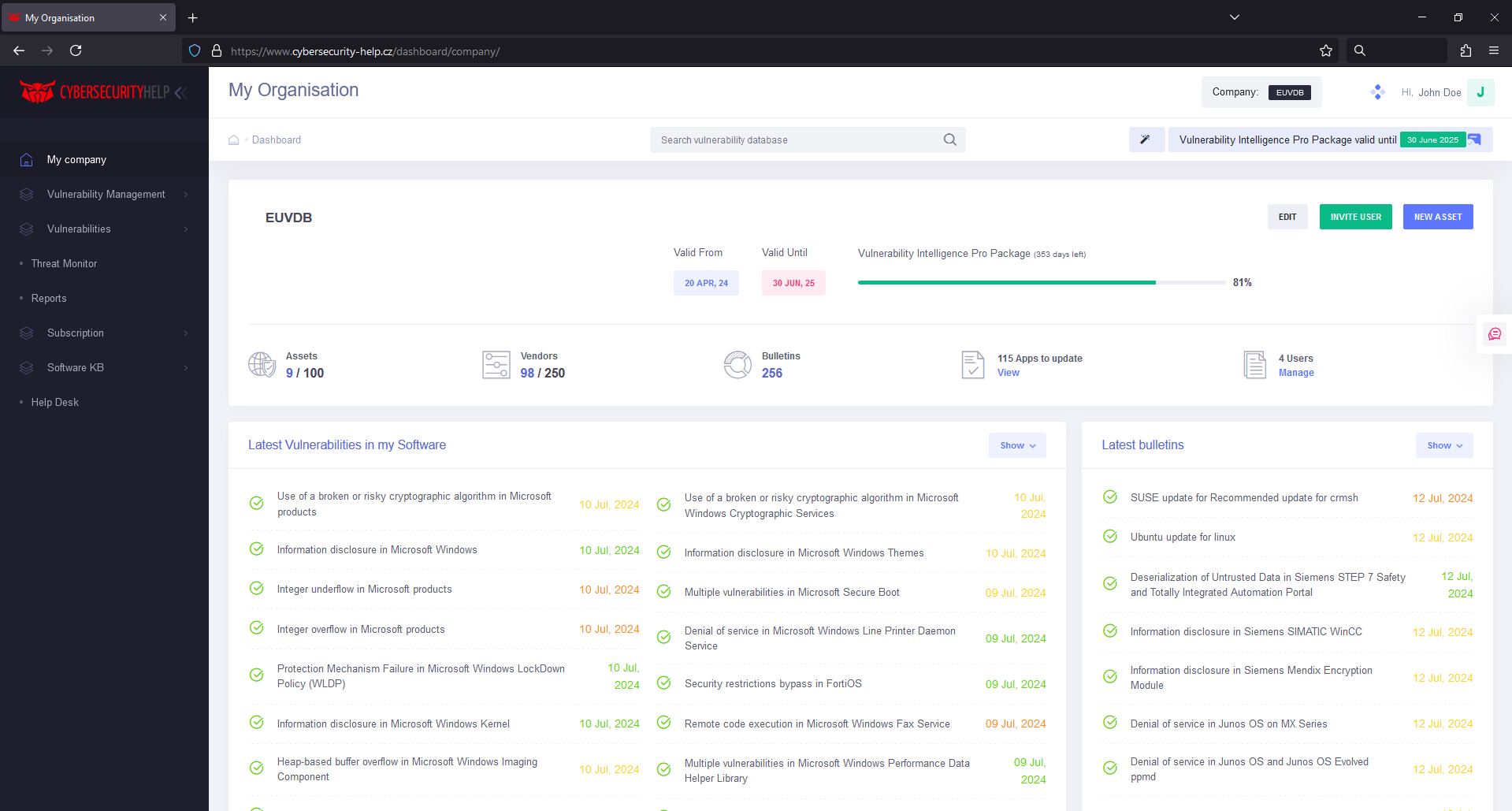
Vulnerability Management Platform
Your vigilant guardian, detecting, prioritizing, and helping you remediate potential threats before they get exploited by hackers.

CSH Agent
A vulnerability scanner tool that can be deployed on desktop and server systems to continuously monitor your company's assets and instantly notify you of ongoing or potential threats.
Vulnerability Management Offers
Comprehensive security solutions tailored to protect your infrastructure
Comprehensive Risk Assessment
Uncover vulnerabilities across your entire network using both agent and agentless approaches.
Intelligent Prioritization
Understand which vulnerabilities need immediate attention so your IT team can plan and execute tasks efficiently.
Actionable Insights
Real-time data on new vulnerabilities, exploits and zero-days, empowering informed decisions to mitigate threats swiftly.
Continuous Monitoring
24/7 security monitoring of your systems, even when offline. No waiting for scan results to detect threats.
Vulnerability Intelligence
Our platform uses a comprehensive database of known vulnerabilities to provide actionable and personalized vulnerability intelligence tailored to your infrastructure.
View Vulnerability Database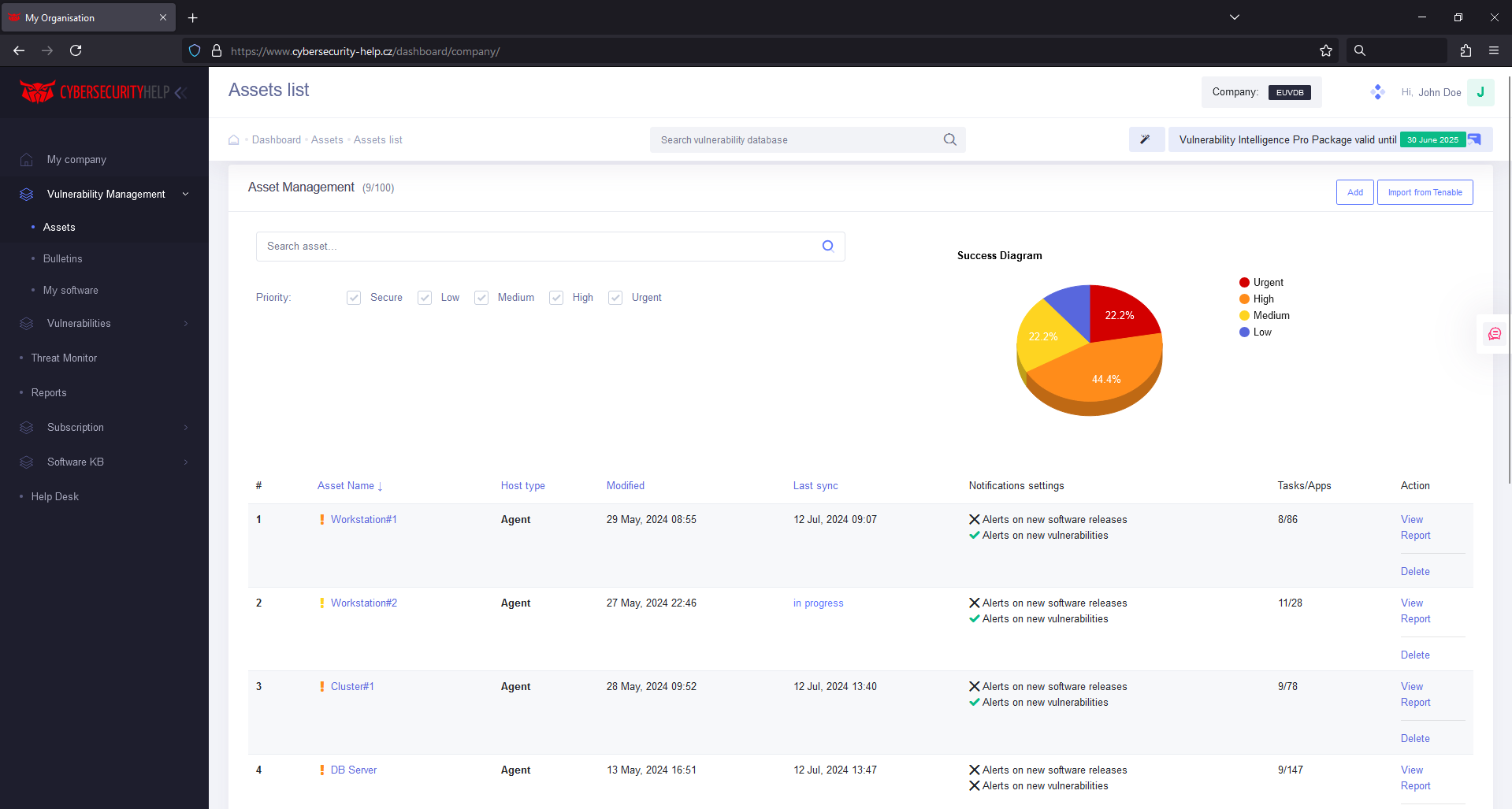
How Does This Work?
Choose the approach that fits your infrastructure
Software Deployment
Download our agent software from our website and deploy it across your desktops and servers. The agent continuously monitors your systems and reports vulnerabilities in real-time.
- Automated vulnerability scanning
- Real-time threat notifications
- Continuous system monitoring

Agent-Free Approach
Manually create assets and assign software without installing agents. Perfect for routers, switches, and hardware that cannot run traditional monitoring software.
- No software installation required
- Hardware-compatible monitoring
- Latest threat alerts

API Integration
Already have a vulnerability management solution? Connect it to our dashboard using our API to enrich your current solution with our comprehensive vulnerability intelligence.
- Seamless integration with existing tools
- Enhanced threat intelligence
- Centralized dashboard access
Connect your existing infrastructure with our powerful API endpoints
Protect Your Systems From Threats
Our vulnerability management platform stands as your vigilant guardian, detecting, prioritizing, and helping you remediate potential threats before they get exploited by hackers.