Credit and debit cards became very common these days. One hardly can imagine a modern life without these tiny slick pieces of plastic. While they are very useful, they also jeopardize cardholders. We hear about data breaches every day, criminals sell credit cards details (numbers, expiration date, and cardholders’ names) on black markets, and more people become victims of identity theft.
Identity theft is the deliberate use of someone else's identity, usually as a method to gain a financial advantage or obtain credit and other benefits in the other person's name, and perhaps to the other person's disadvantage or loss (from Wikipedia).
Forewarned is forearmed, and that is why we are going to tell you how criminals can get your credit card details. Today we are going to talk about one of many techniques crooks use to steal your data dubbed skimming. But first we need to determine ways criminals use to hook your credit card data.
As we mentioned above, crooks can compromise corporate servers containing customer’s payment information. If you at least once purchased something online or did another kind of payment and entered your credit card information, your data was stored on a respective server. In case of lack appropriate security, hackers can compromise this server and steal all the information. Sometimes servers are not properly secure, and their content is available for download by third parties.
The second way is to infect point of sale (POS) systems used in supermarkets, restaurants, hotels, etc. with malicious piece of software (malware). This malware resides inside computer networks and silently steals data from cards inserted in POS systems. Criminals engaged in this kind of cyber crime are called carders. Using your credit card data carders can buy luxury stuff online on your behalf or transfer your money into their own accounts. They also can clone your card (make a copy) and use it to withdraw your money from the ATM.
These two methods require stealing data using certain kind of software. But there is the third technique which requires using special devices along with malware. This method is not intended to hijack corporate networks nor POS systems. This method is about ATM.
For stealing credit card data from the ATM carders use piece of hardware dubbed skimming device or skimmer. Nowadays, cybercriminals dispose skimmers of different types and designs but with general purpose – to steal information from magnetic stripe on your card when you insert it in a card acceptance slot.
So, where can carder get a skimmer? One can make it by himself or buy it online. To find out if we could buy some skimmers online we went to some black markets in a Deep Web we observed in this post. We’ve found the whole skimming toolkit on Tochka web site.
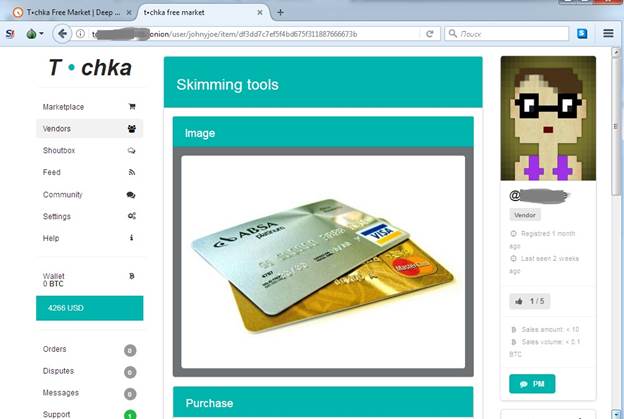
You could only pay $4,255 and get all the tools you need. When we tried to visit Tochka next time the site was unreachable. At the time of writing this article two other websites were unreachable too.
As mentioned above, criminal could make skimming device by himself. We’ve found some parts on the Internet. What’s interesting, some replacement parts which can be used to build skimmers are available on legal web sites such as Ebay or Alibaba.com.
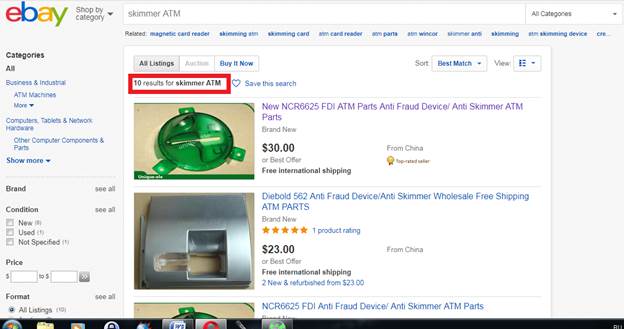
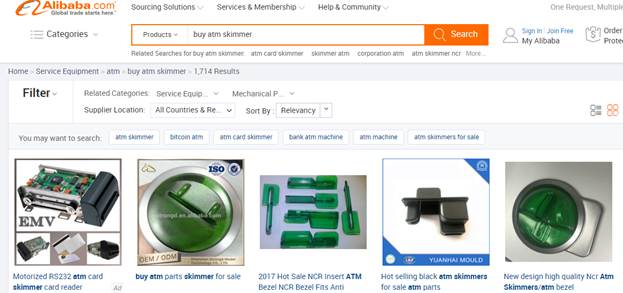
These parts look familiar, don’t they? These are card acceptance slots of an ATM’s card reader. The green ones are so-called anti-skimming devices intended to protrude from the slot to prevent thieves from easily attaching skimmers. But, very often fraudsters use these “anti-skimming” pieces of plastic as a part of skimming devices itself. They connect it to the skimming mechanism, and using glue or adhesive tapes attach the device to ATM. The fake “anti-skimmer” covers the real one, and every time cardholders insert their cards they slip them through the fake slot. You can see one of such devices found in Vienna in this video:
We’ve found this type of skimmers on Tochka web site.
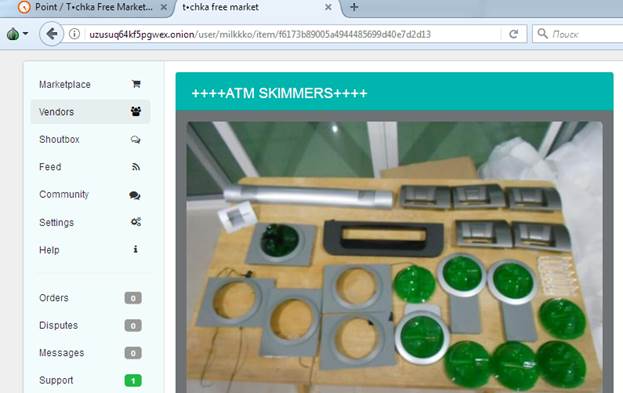
This type of skimmers is very hard to spot. That is why we recommend you to check the slot before you insert your card in an ATM’s card reader. Simply pull it several times, and in case you’re dealing with the skimmer it would unstick like in a video above.
Sometimes criminals are able to steal your credit card data leaving ATM almost untouched. For this purpose they use legal portable card readers attached to the ATM. Victims could confuse the real card reader with the fraudster’s device and insert their cards directly to the skimmer. You can easily and legally purchase these card readers online.
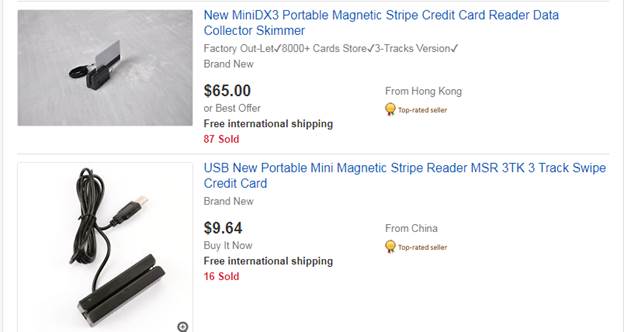
As a precaution measure we recommend you to pay close attention to color and location of a card acceptance device. If its color differs from the color of ATM, or it is located in unusual place you better check it twice.
In one of the online stores – in the clearnet not in the Dark Web – we have found interesting device which turned up to be a cash trapping device. Crooks insert this claw-like gadget in a cash dispensing slot.
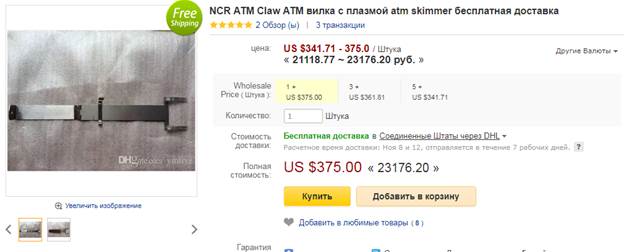
So, before you insert your card, you should check a cash dispensing slot too. In case you find suspicious third party devices, you’d better not use this ATM.
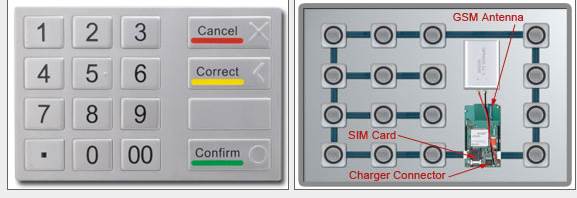
Apart from aforementioned devices for reading credit card data from magnetic stripe or stealing cash from the dispensing slot there is a skimmer for capturing your PIN. It mimics the legitimate PIN entry pad, but its intent is to steal your PIN. The picture below is provided by one of the ATM skimmer seller from Deep Web. As you can see, it looks like legitimate but it has SIM card and GSM antenna to transmit stolen data to cyber criminals. That is why, before using ATM you should try to pull off the PIN entry pad. In case it is fake, it would be separated from the legitimate pad.
By Natalia Galadzhyants
Analyst at Cybersecurity Help