Today Microsoft has released patches for 49 vulnerabilities in total. Extra attention was directed to vulnerability in Windows CryptoAPI implementation, tracked as SB2020011424 (CVE-2020-0601), given that media just before the initial patch released have started speculating on its impact. Additional interest was also caused by the organization, that reported this vulnerability to Microsoft: that was NSA(!).
The vulnerability in question present in the Windows usermode cryptographic library, CRYPT32.DLL, on Windows 10, Windows Server 2016, and Windows Server 2019 systems. As per Microsoft’s description, “a spoofing vulnerability exists in the way Windows CryptoAPI (Crypt32.dll) validates Elliptic Curve Cryptography (ECC) certificates”.CVE-2020-0601 could be exploited by an attacker using a spoofed code-signing certificate to sign a malicious executable, making it appear the file was from a trusted, legitimate source. Furthermore, the user would have no way of knowing the file was malicious, because the digital signature would appear to be from a trusted provider. Microsoft says that this flaw could allow the attacker to launch man-in-the-middle attacks and decrypt confidential information on user connections to the affected software.
The software giant says it has not detected attacks in the wild exploiting the CVE-2020-0601 bug, and it has marked the flaw as “Important”, not “Critical”, but in its own press-release the NSA has warned that it “assesses the vulnerability to be severe” and “that sophisticated cyber actors will understand the underlying flaw very quickly and, if exploited, would render the previously mentioned platforms as fundamentally vulnerable”. To mitigate the threat the agency recommends to install all January 2020 Patch Tuesday patches as soon as possible.
All 49 vulnerabilities were combined into 26 security bulletins, grouped by vulnerable components and issued by Cybersecurity Help. For each vulnerability we assign a risk level, based on our primary analysis.
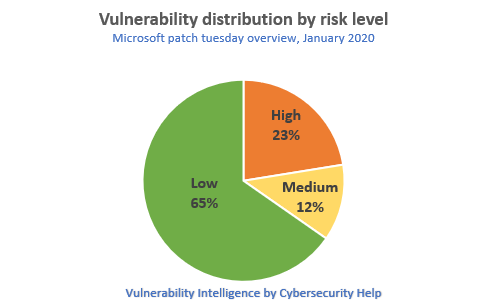
11 vulnerabilities were rated as Highly critical, 6 vulnerabilities as Medium and 32 vulnerabilities had a Low risk assigned.
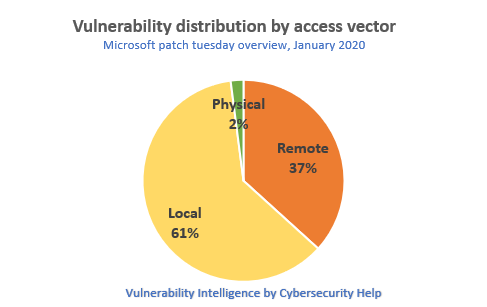
18 vulnerabilities can be exploited remotely, 30 vulnerabilities locally and 1 vulnerability requires physical access to the system.
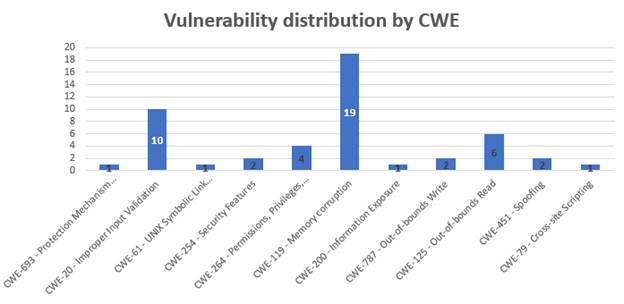
The majority of patched issues (27 out of 49) are boundary errors. 10 vulnerabilities were caused by improper input validation, 4 issues are related to privilege management, as shown below:
Below is a table with the list of all vulnerabilities, patched by Microsoft in January 2020.
| Software | Severity | CVE/CVSS | Known exploits |
| SB2020011449: Security restrictions bypass in Microsoft Windows (1) | |||
|
Windows Windows Server |
Low |
CVE-2020-0644 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:L/I:N/A:N/E:U/RL:O/RC:C |
Not available |
| SB2020011448: Denial of service when processing hardlink in Microsoft Windows (1) | |||
|
Windows Windows Server |
Low |
CVE-2020-0616 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H/E:U/RL:O/RC:C |
Not available |
| SB2020011447: Privilege escalation via symlinks in Microsft Windows (1) | |||
|
Windows Windows Server |
Low |
CVE-2020-0635 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2020011446: Security restrictions bypass in Windows 10 (1) | |||
|
Windows Windows Server |
Low |
CVE-2020-0621 CVSS:3.0/AV:L/AC:L/PR:H/UI:N/S:U/C:N/I:H/A:N/E:U/RL:O/RC:C |
Not available |
| SB2020011444: Privilege escalation in Windows Media Service (1) | |||
|
Windows Windows Server |
Low |
CVE-2020-0641 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2020011443: Privilege escalation in Microsoft Update Notification Manager (1) | |||
|
Windows Windows Server |
Low |
CVE-2020-0638 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2020011442: Remote code execution in Microsoft Excel (3) | |||
|
Microsoft Office Microsoft Excel Microsoft Office for Mac |
High |
CVE-2020-0650 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2020-0651 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2020-0653 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2020011441: Privilege escalation in Microsoft Windows Subsystem for Linux (1) | |||
|
Windows Windows Server |
Low |
CVE-2020-0636 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2020011440: Remote code execution in Windows Remote Desktop Client (1) | |||
|
Windows Windows Server |
Medium |
CVE-2020-0611 CVSS:3.0/AV:N/AC:H/PR:N/UI:R/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2020011439: Multiple vulnerabilities in Windows Remote Desktop Gateway (RD Gateway) (3) | |||
| Windows Server | High |
CVE-2020-0609 CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2020-0610 CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2020-0612 CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H/E:U/RL:O/RC:C |
Not available |
| SB2020011438: Information disclosure in Microsoft Remote Desktop Web Access (1) | |||
| Windows Server | Medium |
CVE-2020-0637 CVSS:3.0/AV:N/AC:L/PR:L/UI:R/S:U/C:H/I:N/A:N/E:U/RL:O/RC:C |
Not available |
| SB2020011437: Denial of service in Microsoft Hyper-V (1) | |||
|
Windows Windows Server |
Low |
CVE-2020-0617 CVSS:3.0/AV:L/AC:H/PR:H/UI:N/S:C/C:N/I:N/A:H/E:U/RL:O/RC:C |
Not available |
| SB2020011436: Multiple vulnerabilities in Microsoft ASP.NET Core (2) | |||
| ASP.NET Core MVC | High |
CVE-2020-0602 CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H/E:U/RL:O/RC:C CVE-2020-0603 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2020011435: Multiple vulnerabilities in Microsoft Windows Common Log File System Driver (3) | |||
|
Windows Windows Server |
Low |
CVE-2020-0615 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N/E:U/RL:O/RC:C CVE-2020-0639 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N/E:U/RL:O/RC:C CVE-2020-0634 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2020011434: Multiple privilege escalation vulnerabilities in Windows Search Indexer (12) | |||
|
Windows Windows Server |
Low |
CVE-2020-0614 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2020-0613 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2020-0623 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2020-0633 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2020-0632 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2020-0631 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2020-0630 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2020-0629 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2020-0628 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2020-0627 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2020-0626 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2020-0625 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:C/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2020011432: Multiple vulnerabilities in Microsoft .NET Framework and Core (3) | |||
|
Microsoft .NET Framework Microsoft .NET Core |
High |
CVE-2020-0605 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2020-0606 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2020-0646 CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2020011431: Privilege escalation in Microsoft Cryptographic Services (1) | |||
|
Windows Windows Server |
Low |
CVE-2020-0620 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2020011430: Remote code execution in Microsoft Internet Explorer (1) | |||
| Microsoft Internet Explorer | Medium |
CVE-2020-0640 CVSS:3.0/AV:N/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2020011429: Spoofing attack in Microsoft Office Online (1) | |||
| Office Online Server | Medium |
CVE-2020-0647 CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N/E:U/RL:O/RC:C |
Not available |
| SB2020011428: Remote code execution in Microsoft Office (1) | |||
| Microsoft Office | High |
CVE-2020-0652 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2020011427: Security feature bypass in Microsoft OneDrive for Android (1) | |||
| Microsoft OneDrive for Android | Low |
CVE-2020-0654 CVSS:3.0/AV:P/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |
| SB2020011426: Cross-site scripting in Microsoft Dynamics 365 (On-Premise) (1) | |||
| Microsoft Dynamics 365 Field Service (on-premises) | Low |
CVE-2020-0656 CVSS:3.0/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N/E:U/RL:O/RC:C |
Not available |
| SB2020011425: Multiple vulnerabilities in Microsoft Graphics Components (2) | |||
|
Windows Windows Server |
Low |
CVE-2020-0607 CVSS:3.0/AV:L/AC:L/PR:L/UI:R/S:U/C:H/I:N/A:N/E:U/RL:O/RC:C CVE-2020-0622 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N/E:U/RL:O/RC:C |
Not available |
| SB2020011424: Spoofing attack in Microsoft Windows CryptoAPI (1) | |||
|
Windows Windows Server |
High |
CVE-2020-0601 CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:N/E:U/RL:O/RC:C |
Not available |
| SB2020011423: Information disclosure in Microsoft Windows GDI+ (1) | |||
|
Windows Windows Server |
Low |
CVE-2020-0643 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N/E:U/RL:O/RC:C |
Not available |
| SB2020011422: Multiple vulnerabilities in Microsoft Win32k (3) | |||
|
Windows Windows Server |
Low |
CVE-2020-0642 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C CVE-2020-0608 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N/E:U/RL:O/RC:C CVE-2020-0624 CVSS:3.0/AV:L/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H/E:U/RL:O/RC:C |
Not available |